How is surveillance carried out?
This video summarizes and explains the methods used by the NSA to carry out surveillance on global citizens.
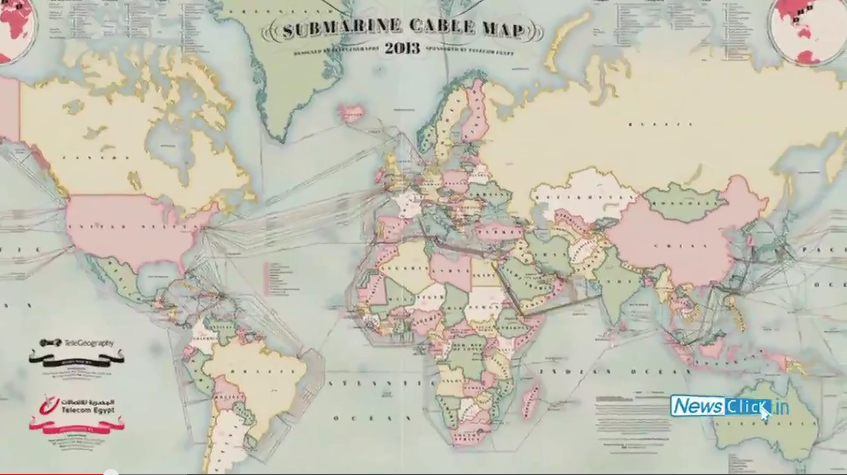
Transcript:
Rishab Bailey (RB): Hello and welcome to Newsclick, in part two of our series of videos on NSA surveillance. In this video we discuss various technical issues related to what we know is the Global Surveillance Program of the NSA.
Nagarjun Kandukuru (NK): Contrary to popular misconception, the Internet is not an ethereal concept. In fact it relies on a backbone of infrastructure providers comprising physical things such as fiber-optics, wires, routers and servers which, of course, are located in different country. When you make a phone call from Delhi to Sao Paulo, it might surprise you to know that it goes through the US. In effect, the US is the switchboard of the world. Most Internet and telephone traffic flows through optic fibers, undersea cables and satellites. For historical reasons much of it flows through America. This makes it easy for American intelligence agencies, like the NSA, to intercept data which flows right through their living rooms. Separately, US corporations such as Cisco and HP dominate the world's hardware market, the PCs and routers we all use. As the latest Der Spiegel revelations show, the products manufactured by these corporations are, to say the least, suspect. So devices that are necessary for Internet infrastructural work, ranging from routers to service tax, are all probably compromised. It has become clear over the last year or so that the entire physical infrastructure that compromises the Internet is largely controlled by America.
RB: Above the infrastructure layer is what can broadly be termed the 'protocols and transport layer' that enables information to be sent from one computer to another. An essential component of this layer is the DNS system.
NK: When you type in www.rediff.com say, it is the DNS system that tells your computer where to fetch the relevant data from. This DNS system functions in a hierarchical fashion with America controlling the core root zone files through two US based corporations known as ICANN and Verisign. This gives the US the ability to add, delete and modify domain names as per their will. They could notionally delete the entire 'dot in' domain name which of course belongs to India, if Obama got out of the wrong side of bed. In addition to the DNS system, the US has also co-opted MOST standard setting and protocol related bodies such as the IETF, IANA etc. Crucially, they also appear to have subverted institutions such as the National Institute of Standards and Technology. It attempts to ensure appropriate standards of encryption. The NSA has built a variety of programmes that look to exploit weaknesses in the standards and protocols that govern the Internet such as Xkeyscore, MARINA and Pinwale. Such programmes have allowed the US to attack even supposedly safe websites that use 'https'.
RB: The third layer is how you as a user access the Internet or what could be broadly be termed 'access devices'. We all need an end to end user device such as a phone or laptop to access the Internet. Not only has the NSA been working with, and sometimes without the knowledge of the relevant corporations who create these devices, they have inserted back doors into pretty much every American product. They also ensure that they can insert further devices into electronic products by monitoring online sales requests and intercepting packages before they can be delivered to your doorstep. The final layer is the 'application layer'. You're probably most familiar with this layer of the Internet, the Googles, the Facebooks and Yahoos that we've all grown to love. What few people realise however, is the complete and total monopoly these US based corporations enjoy over the online marketplace. As shown in the data presented, Google and Facebook have monopolies the kinds of which have never been seen including the years of oil and railroad monopoly in the United States. This vast pool of resources in the form of user data makes these corporations ideal allies for the US Government. No one is very sure if these corporations are arm twisted into providing data to the NSA or whether this is done using clandestine methods, but it is clear, as shown in the PRISM slides, that the NSA has access to the databases of these big Internet MNCs.
NK: All this leads to a rather depressing picture in terms of what the Internet was supposed to be and what it has become. In the next video in this series we'll look at ways in which you, an ordinary user, can fight back against the might of the NSA.
Get the latest reports & analysis with people's perspective on Protests, movements & deep analytical videos, discussions of the current affairs in your Telegram app. Subscribe to NewsClick's Telegram channel & get Real-Time updates on stories, as they get published on our website.
























